I’ve made two minor changes to the site today:
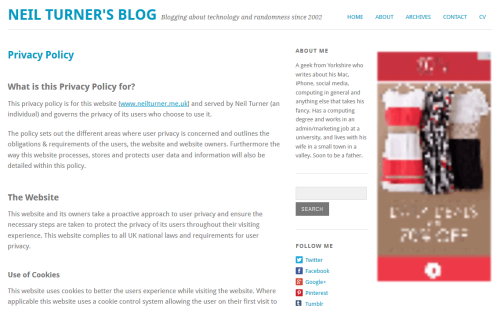
- There is now a privacy policy available to view
- The first time you visit this site from today, you will be asked for permission to store cookies on your computer
These come about because of my participation with Google AdSense – all EU sites must obtain user consent for cookies with effect from the end of September. This is the so-called ‘EU Cookie Directive’.
As you may guess from my tone, I’m not particularly happy about this. I accept the need for a privacy policy and I should have probably had one already, but I hate the popup cookie consent messages that sites use. There’s a lack of consistency, they offer a particularly poor user experience to mobile users (obstructing a large part of the page) and I bet almost nobody actually reads the privacy policies anyway.
The privacy policy is adapted from this example, and I’m using the Cookie Law Info WordPress plugin to generate the messages. The plugin is really simple and you can set it up in a few minutes. There’s no need to edit any templates, but you can still customise it.
P3P
I really wish that, following the EU Directive that mandated consent for cookies, that there had been some collaboration between web site owners and web browser vendors to come up with a more graceful solution. Whilst I accept that it’s best if users are able to consent to cookies being stored on individual web sites, this could have been done in a standardised way as a function of the user’s web browser.
Years ago, the W3C proposed P3P, which used HTTP headers and machine-readable privacy policies to allow users to select a level of privacy that they were comfortable with. Anything else, such as third-party cookies, would be blocked if desired. Ironically for a web standard, the only current web browser that supports P3P is Microsoft’s Internet Explorer, which has done since version 6. It remains an opt-in and rarely-used standard and the W3C paused all work on it ages ago.
I haven’t researched P3P enough to know whether it could be developed further, so that web sites can use it for EU Cookie Directive compliance. If it could, and if Google, Mozilla, Apple, Opera and others all agreed to implement it, then the web could become a less annoying place. Especially if there was an option to implicitly accept all cookies from all first-party web sites, for example.